Products for the Dental Industry

The Top 10 Things You Need to Know to Recognize and Avert Cyber Attacks
Robert McDermott, President and CEO, iCoreConnect
Cyber attacks are hitting too close to home in the dental industry. The American Dental Association was attacked in April by a new ransomware gang, resulting in service disruptions to dentists and dental associations nationwide.
According to Verizon’s 2022 Data Investigation Report, ransomware breaches increased by 13%, and 82% of breaches involved the “human element.” One of the easiest ways for these aggressive cyber gangs to get into your system is through email trickery. Phishing emails will look like they come from a legitimate source. They may be personalized to appear to be from a trusted person or company. They want you to take a seemingly harmless action, like making a phone call, clicking a link, or providing login or other information that gives them a key to hold your practice hostage. Then they demand a ransom in order for you to get your practice up and running again.
Using real examples, here are the 10 things you need to know about what cyber criminals are doing to target you and what you can do to avert catastrophe.
1. The sender requests you call a phone number.
Example:
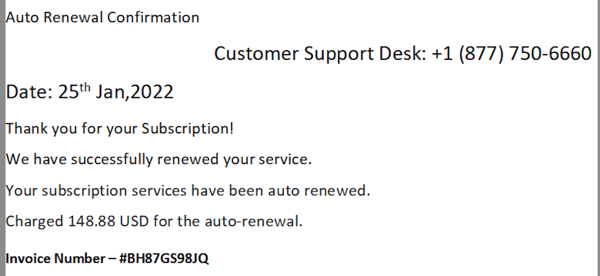
What they're doing: Once you call, the person posing as a customer service representative will try to convince you of a couple of things. You may be told to go to an online site and put in a code or other information to request a refund. The scammers may also tell you that you accepted a free trial of the product several years ago and now they need to log on to your computer to delete the program. They may request bank information so that they can “refund” the money. A real company will not request this information from you.
2. The sender’s name looks legitimate, but the email address is spoofed or doesn’t remotely resemble the company it claims to be.
Example:
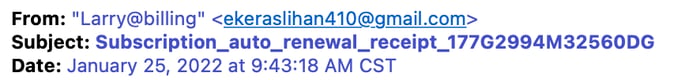
What they're doing: The cyber crime group expects you to read quickly and think the email is coming from a trusted source. A closer look reveals the name in the “From” line and the email address are inconsistent, both with each other and the actual company they claim to represent. This nuanced detail is often missed when rapidly scanning through the pile of emails in your inbox. In this case, the criminals claim to be Microsoft.
3. Logos and company names are too prominently placed in the email.
Example:

What they're doing: Cyber criminals want to appear credible. They use every possible asset to convince you to take the action requested. But sometimes the logos are just a little off. These are blurry and the layout isn’t consistent with the way Microsoft presents them on its website.
4. Logos, company name and sender emails are often at odds.
Example:
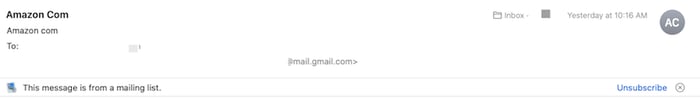
What they're doing: Blurry logos aren’t the only sign an email might not be credible. The criminals may also include what appears to be the company web address or company name. In this example, Amazon is represented as “Amazon Com.”
5. You have to click a link to take action.
Example:

What they're doing: This email combines several tactics addressed thus far. In addition, the “sign in” link is embedded so you can’t see where it actually takes you unless you hover over it without clicking. The fake sender hopes you won’t think to check the URL before clicking. Once you click, you’ve possibly exposed yourself to any kind of malware, including ransomware, which can shut down your practice and stick you with a very high price for data recovery.
NOW, HERE'S WHAT YOU SHOULD DO TO AVERT EACH ATTACK.
6. Never call the phone number provided.
What You Should Do: If you call the number provided, they’ll likely ask you to provide information they can use to access your private or bank details. Avoid the trick by checking your bank or credit card account before you take any action. Call your bank or credit card company to report the suspicious email and alert them to monitor your account. As an additional check, visit the supposed source’s actual website to look up the correct number for support or account issues.
7. Catch the sender info mismatch.
What You Should Do: Always look at the “From” line with care. This is often your first line of defense. If information in the sender’s name or email address doesn’t match, it’s an indication the source is not legitimate. Now you can cautiously discern if the rest of the email bears action.
8. Poor logo quality means suspicious sender.
What You Should Do: Taking note of details like extremely oversized or fuzzy logos helps you zero in on a non-legit sender. You can clearly see the big picture (pun intended) intent of a phishing email. If you’ve ever received communication from the legitimate source, compare previous emails.
9. If logos and names don’t agree, question the security.
What You Should Do: Pay attention to the details. Using “Amazon com” in the “From” line is a poor attempt to pretend they’re Amazon. It’s not a verified email, business name or web address. If you’re in doubt, search the company to see if the actual company information aligns with the email.
10. Always hover before you click.
What You Should Do: Embedded links may seem convenient, but they’re also a quick way to get you to click on something malicious. Before you click, hover your cursor over the link and you should see a small pop-up indicating the URL it points to. A false hyperlink will look something like http://www.FAKEURL.com/FAKE KEY WORDS/COMPANY NAME. If it looks remotely suspicious, don’t click the link!
When you receive an email you think is suspicious for any of these reasons, after you take the proper action to avert the attack, be sure you alert your IT personnel as well as the rest of your team. You may not be the only door the cyber criminal is knocking on, but you can be the first line of defense to protect your whole team.
Equally important is the type of email service you are using, especially when sending or receiving Protected Health Information (PHI). Make sure your email is encrypted at the highest level, transmitted across a private network and in compliance with every federal HIPAA requirement. The most secure, compliant email requires your office to initiate emails with anyone outside your verified network of contacts. The best protection is to keep criminals from getting to your inbox in the first place.
MDA Services endorses iCoreExchange secure, HIPAA-compliant email by iCoreConnect. iCoreExchange not only exceeds requirements to protect your practice and patient data, it also allows you to attach as many large files as you want to any single email. Speed up your workflow, protect patients and your practice. Scroll down to learn more about iCoreExchange, along with other endorsed products from iCoreConnect. MDA members receive a substantial discount on iCoreExchange.
Endorsed technology options to
speed practice workflow and increase revenue.
HIPAA Compliant Email & Referral Network
HIPAA-compliant email where big attachments are no big deal. Watch the video.
| Retail | 35 / mo. |
| Member Discount | 35% |
| Member Rate | 22.50 / mo. |
Cloud Electronic Prescribing
e-Prescribe all meds faster from any device. Option to connect to Michigan Prescription Monitoring Program (PMP / MAPS). Watch the video.
| Retail | 79 / mo. |
| Member Discount | 43% |
| Member Rate | 45 / mo. |
| Add EPCS | 9 / mo. |

REVENUE DASHBOARD
iCoreHuddle gives you the power to instantly reveal revenue potential for each patient in one intuitive dashboard. Watch the video.
| Retail | 199 / mo. |
| Member Discount | 25% |
| Member Rate | 149 / mo. |
PRACTICE MANAGEMENT WITH A MIND FOR BUSINESS
iCoreDental offers you the customization and integrations you need for your practice, and is scalable to grow with you to manage unlimited locations. Watch the video.
| Member Discount | 33% |

- MDA Members Only -
These discounts are exclusively for members verified by the MDA roll. If you are not currently a member, your iCoreConnect sales rep would be happy to introduce you to the folks at MDA.